2 個答案
- 最新
- 最多得票
- 最多評論
2
Hi,
According to other re:post answers, It is not possible to configure the ELB to do not expose that header.
However, as a workaround, you can override the value using CloudFront edge functions.
Note even when using. Cloudfront the alb will have to be public still(internet facing). Even if you could mask the server header the IP addresses are registered with AWS
0
It is not possible to hide this header directly on Application Load Balancer. Use Amazon CloudFront's Response Headers Policies instead. Please see my response to a similar question on re:Post, on How to prevent "awselb/2.0" server information exposure in HTTP response header.
已回答 14 天前
相關內容
 AWS 官方已更新 2 年前
AWS 官方已更新 2 年前
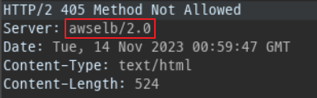
Also, consider opening a support case, and express your use-case why you want to be able to override this header.